Professor Jean Camp of Indiana University’s Security and Privacy in Informatics, Computing and Engineering (SPICE), and Zheng Dong of Microsoft Research (formerly of Indiana University; Dong received his Ph.D. in Security Informatics in 2015) were approved for a patent on October 11th, 2018. This patent (US 20180294978) is the result of research on systems and methods for public key certificate identification and made possible by support from the Department of Homeland Security.
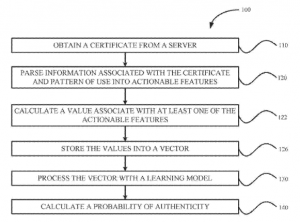
The patent is for a learning certificate authentication system made of a certificate downloader (for procuring the certificate), a feature extractor (to communicate with the certificate downloader), a processor, and non-transitory memory (which following processor execution initiates the processor calculating the authenticity probability based on a processed vector). The configuration of the feature extractor allows it to parse information associated with the certificate as well as usage patterns into actual features, in addition to calculating a value associated with one or more features. An overview of the process is shown in the diagram below.
Certificate authentication is integral in preventing incidents when an attacker manipulates a victim’s trust by masquerading as a legitimate source, often referred to as an exemplary attack.
Examples of exemplary attacks include phishing and pharming. Public key certificates are helpful in thwarting such attacks. Still, such infrastructure can fall short of providing the necessary authentication measures for many organizations, especially if they are small to medium size.
There are five main instances where public key infrastructure falls short of ensuring authentication. First, if the set of facts within the signature of the public key is incorrect as a result of incorrect issuance or of changes in the signature over time. Second, when flaws exist in the cryptography, for example in the hash value or digital signature. Third, if software necessary to confirm certificate authenticity is flawed, making it likely incorrect or false certificates could be authenticated. Fourth, when end user perception of the meaning of the certificate is often at odds with the intended issuance and connotation of the certificate. Lastly, a fifth issue for public key infrastructure regarding authentication is revocation. The revocation process poses a challenge for the current state of public key certificates due to irregular behavior of browsers and web application clients when checking revocation status.
This work by Camp and Dong is an invaluable improvement to the landscape of public key infrastructure as it addresses the previous infrastructural issues listed above and is more suitable for small to medium organizations.